
Scalability and Device Profiles in Lyra Sample Game for Unreal Engine | Unreal Engine 5.0 Documentation
GitHub - SteamDatabase/FileDetectionRuleSets: 🔎 Rules to detect game engines and other technologies based on Steam depot file lists
Scalability and Device Profiles in Lyra Sample Game for Unreal Engine | Unreal Engine 5.0 Documentation

Study on copyright and new technologies. Copyright data management and artificial intelligence by Agence luxembourgeoise d'action culturelle - Issuu


![Editing Units [Command & Conquer: Red Alert 2] [Tutorials] Editing Units [Command & Conquer: Red Alert 2] [Tutorials]](https://images.gamebanana.com/img/ss/tuts/4f6204be6c1cb.webp)



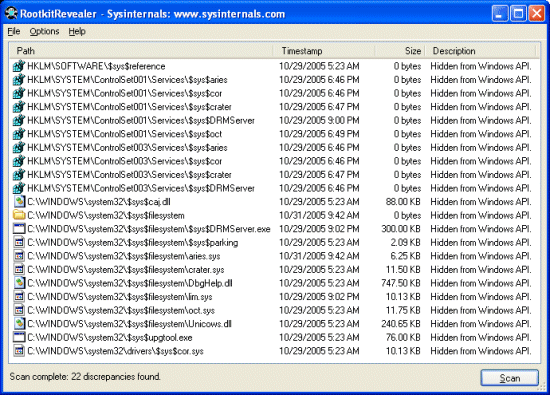



![Tutorial] How to use detected DLL without BAN Tutorial] How to use detected DLL without BAN](https://i.imgur.com/1pyJHkD.png)

